A “sophisticated and alarming” Mac malware attack is being carried out in the guise of free versions of popular apps like the screen recording utility Loom, cryptocurrency manager LedgerLive, and MMO game Black Desert Online.
It appears to be a well-organized attack, with the fake Mac app offers promoted through a combination of legitimate-looking Google ads and phishing emails …
The malware campaign was discovered by Moonlock, a cybersecurity group within MacPaw, the developer behind the CleanMyMac app. The team says that initially it appeared to be limited to mimicking Loom.
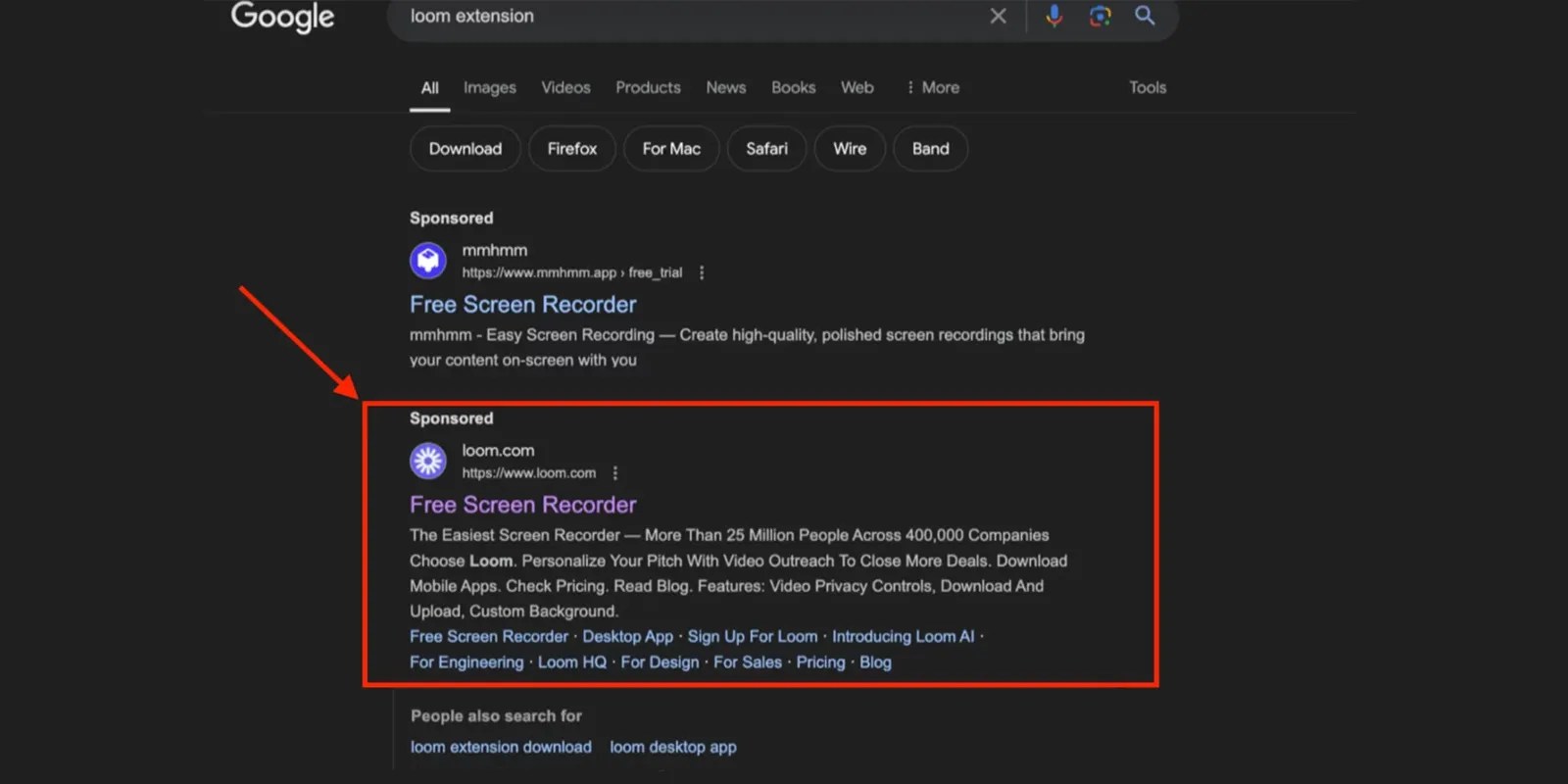
At Moonlock Lab, we’ve recently uncovered a sophisticated and alarming threat spreading through Google-sponsored URLs. The threat, a stealer malware targeting macOS, poses as the popular application Loom, a widely used screen recording tool.
Our investigation kicked off when we noticed a Google ad that appeared to promote the official Loom application. At first glance, it looked legitimate, enticing users to click on what seemed to be a trusted source. However, upon clicking the link, things took a nasty turn.
But further investigation found that ads and promos for other apps were also being used to push the same malware. These include:
- Black Desert Online
- Calendly
- Chrome
- Figma
- Firefox
- Gatherum
- LedgerLive
- PartyLauncher
- Safari
- Zoom
At least one of the phishing campaigns specifically targets YouTube creators, claiming to offer them a creator-specific download link to Black Desert Online.
The LedgerLive link is especially dangerous as, when downloaded, it replaces the real app.
By replacing the genuine app with a harmful version, attackers can potentially access and drain victims’ cryptocurrency wallets. This can lead to financial losses, as the malicious clone is designed to closely mimic the legitimate app’s appearance and functionality, making it difficult for users to detect the compromise.
[It is capable of] grabbing files, hardware information, passwords, data from browsers, keychain dump credentials, and more.
A well-organized group known as Crazy Evil is believed to be behind the campaign.
As always, only ever download apps from the Mac App Store or trusted developer sites, and check that the URL doesn’t change to a different domain when hitting the download link.
FTC: We use income earning auto affiliate links. More.

 3 months ago
31
3 months ago
31








 English (US) ·
English (US) ·