Mishaal Rahman / Android Authority
TL;DR
- Android 15 is adding a built-in mechanism to protect your device from “juice jacking” attacks.
- Charging will be allowed when lockdown mode is enabled in Android 15, but USB data access will not.
- Juice jacking is a largely theoretical problem you don’t really need to worry about, but it’s still nice that Android will protect you against it.
You may have heard of a problem called “juice jacking” recently. It’s a hacking method that involves secretly sending data payloads from a USB cable that you think is only charging your device. These data payloads can theoretically compromise your device or cause it to take some action unbeknownst to you. However, in reality, the threat of juice jacking is so minimal to almost be ignorable, but if you’re still wary of public charging stations, Android 15 has you covered.
Juice jacking takes advantage of the fact that most devices don’t block USB data signaling, i.e., data being transferred over USB, by default. That means that, while on the surface, a USB cable you plug your phone into might seem innocuous, in reality it might be attempting to send some payload to commandeer your device. That payload could consist of keyboard commands that try to brute force the lock screen and then install and launch some malicious app, or it could trigger an exploit in the USB protocol or take advantage of the way USB data is handled by certain components.
Putting aside the impracticality of attackers deploying juice jacking at a large scale, most Android devices are already protected against these kinds of attacks. Nearly every Android device requires the keyguard to be unlocked before USB debugging can be enabled for a particular ADB client, meaning payloads that try to send ADB commands to compromise or commandeer a device will fail. Most Android devices time out when an incorrect PIN, password, or pattern is entered multiple times, causing a brute-force approach to take too long. Finally, Android doesn’t allow access to the device’s external storage until the user unlocks the device and changes the USB mode to “File Transfer/Android Auto” (MTP), preventing the user’s files from being exfiltrated without their knowledge.
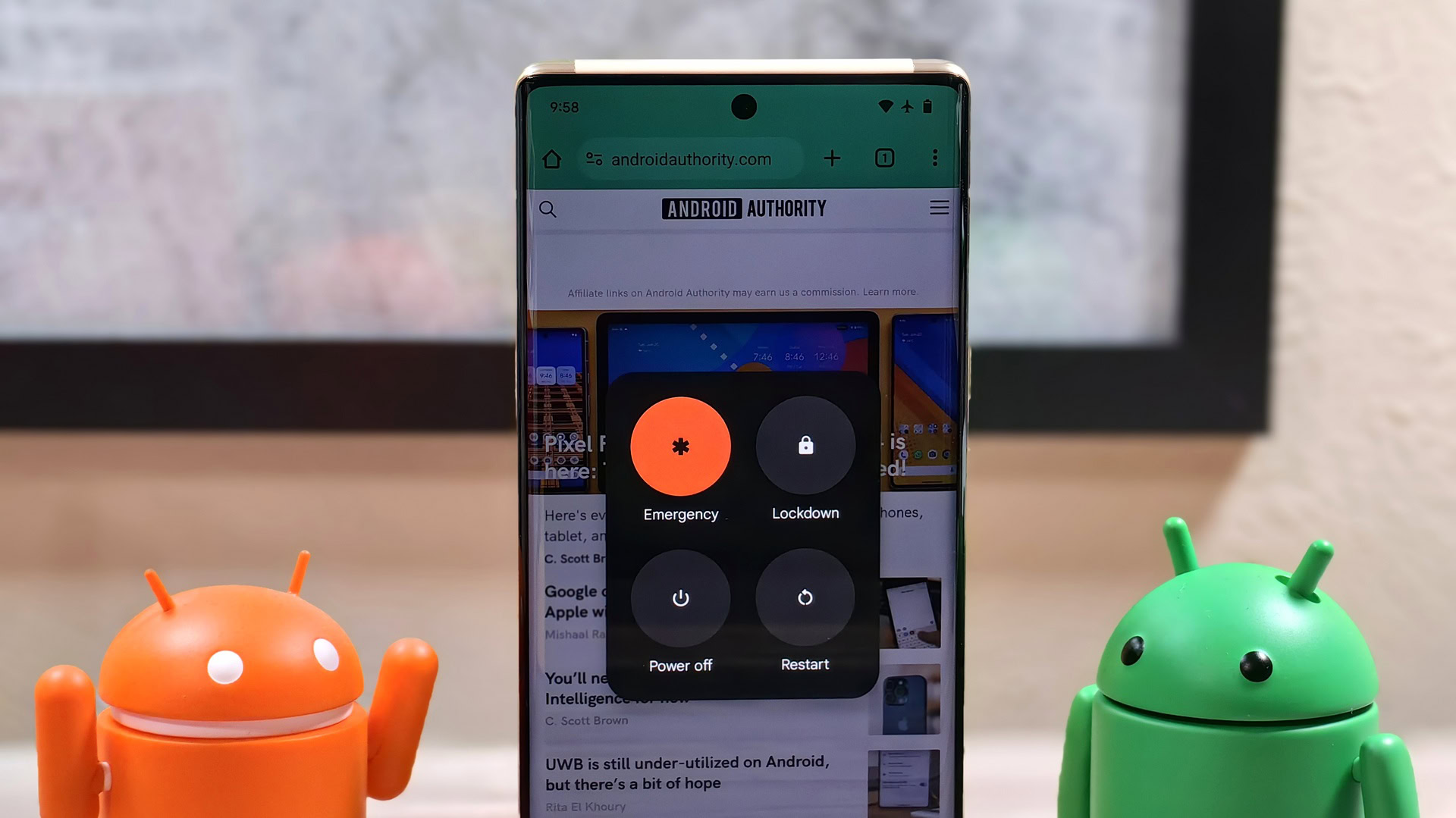
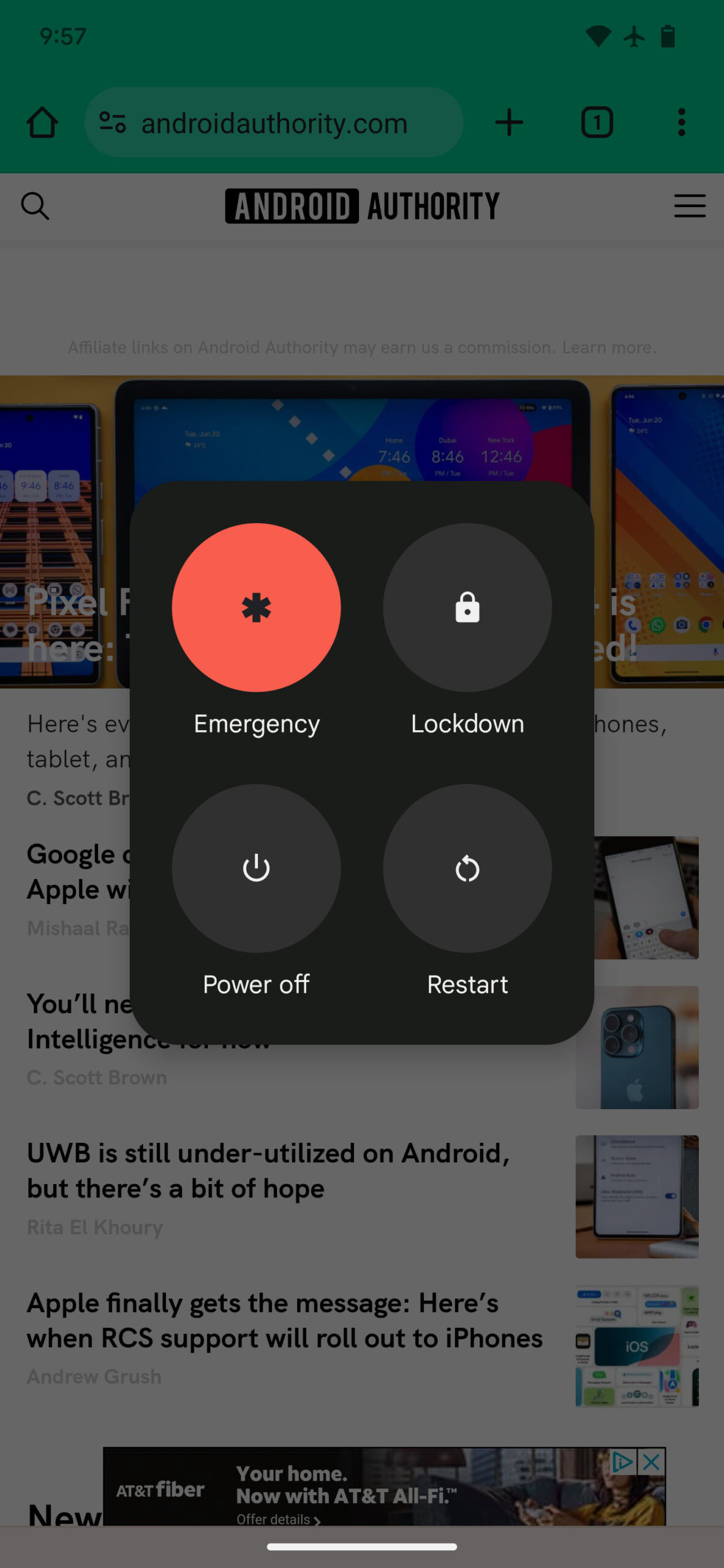
Even though I really think you shouldn’t worry about juice jacking attacks, I can’t guarantee that it’ll never happen to your device. Fortunately, Android 15 is adding a built-in mechanism to protect your device from these attacks. If you hold down the power button to open the power menu and then tap Lockdown to enable lockdown mode, Android 15 will immediately disable USB data access.
Mishaal Rahman / Android Authority
I tested this with a PC that was connected to my Pixel 6 Pro running Android 15 Beta 2.2 via a USB-C cable, and I was immediately kicked out of ADB shell. When I disconnected and reconnected the USB-C cable, I couldn’t re-enter ADB shell until I unlocked the device. The same thing happened when I connected a USB keyboard to my device and then enabled lockdown mode; my keyboard was no longer recognized after enabling lockdown mode in Android 15. However, when I tested the same things on a Pixel phone running Android 14, ADB shell commands and keyboard inputs were still read.

Mishaal Rahman / Android Authority
Lockdown mode was introduced in 2018’s Android 9 Pie release as an optional feature users could add to their power menu. When enabled, lockdown mode hides notifications and disables all forms of authentication except for the user’s primary authentication (PIN, password, or pattern). In Android 12, Google made the lockdown mode toggle appear by default in the Android power menu, though some OEMs hide it or offer their own, similar version of the feature elsewhere. With this upgrade in Android 15, lockdown mode now gives users better protection from anyone looking to exfiltrate data or take control of their devices.
However, it’s worth noting that some devices running Android 15 might not be able to use this feature. That’s because in order to support this functionality, OEMs have to update their device’s USB hardware abstraction layer (HAL) to support the data signaling APIs. Google doesn’t seem to require OEMs to support these APIs, so some devices out there may not support the enhanced lockdown mode on Android 15.
In any case, you shouldn’t really need this feature anyway, given everything I’ve mentioned about juice jacking. If you’re still somehow concerned about juice jacking attacks after reading this article and you can’t wait for the Android 15 update (or know it won’t be coming to your device), then you can buy something like the OSOM Privacy Cable, which has a built-in switch to disable USB data signaling.
Got a tip? Talk to us! Email our staff at [email protected]. You can stay anonymous or get credit for the info, it's your choice.





 English (US) ·
English (US) ·