
We recently reported on how multiple pirate streaming apps for iOS managed to get approved on the App Store by tricking the review process. Although we briefly mentioned some of the techniques used by these developers, 9to5Mac has now taken a deep dive into how these apps are engineered to trick Apple.
Techniques used by developers to bypass the App Store review
Last month, an app called “Collect Cards” reached the top of the App Store’s ranking of the most downloaded free apps in some countries. After our report, Apple took the app down – but many other versions of the same app were later released on the App Store. But how exactly are developers able to trick the App Store review team?
In our original report, we explained that these apps use geofence to prevent anyone at Apple from seeing what the app is actually capable of. But by analyzing the code of these apps, we now have a better idea of how this happens.
As we guessed, these apps share the same code base – even if they are distributed by different developer accounts. They’re built on React Native, a cross-platform framework based on JavaScript, and use Microsoft’s CodePush SDK which allows developers to update parts of the app without having to send a new build to the App Store.
Building React Native apps and using CodePush is not against App Store rules. In fact, there are many popular apps that do so. However, malicious developers take advantage of these technologies to bypass the App Store review.
One of the apps analyzed by 9to5Mac points to a GitHub repository that seems to provide files for multiple pirate streaming apps. This app also uses a specific API to check the location of the device based on the IP address. It returns data such as the country, region, city, and even estimated longitude and latitude.
When the app is opened for the first time, it waits a few seconds to call the geolocation API. This way, the App Store’s automated review process doesn’t see anything unusual in the app’s code. We also checked the app’s behavior by running it through a proxy to fake our location to San Jose, California. For this location, the app never reveals its hidden interface.
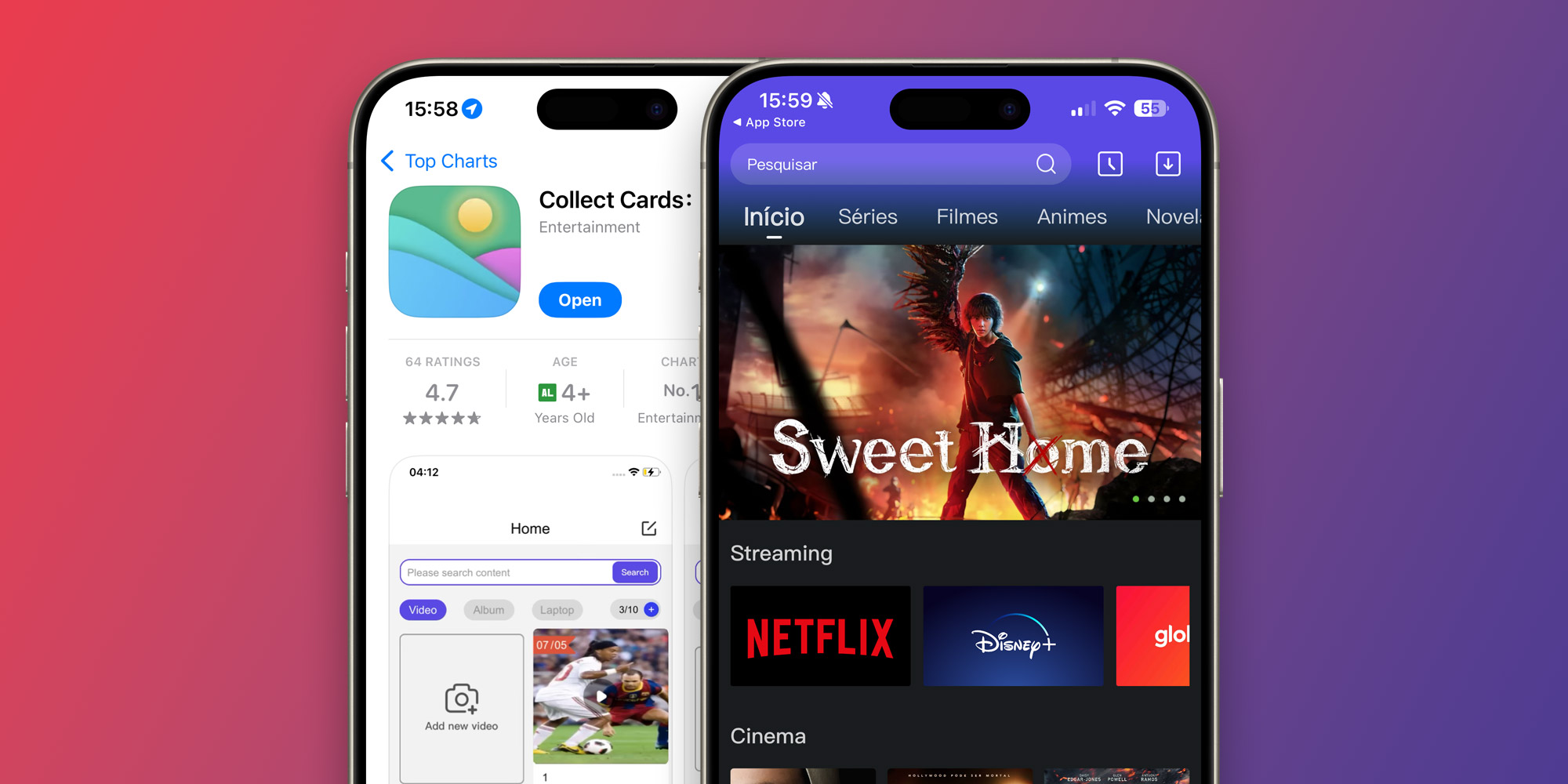
After Apple approves the app with its basic functionalities, developers use CodePush to update it with anything they want. The app then reveals its true interface in “safe” locations.
What can Apple do about it?
Of course, Apple is not immune to apps trying to trick its review system. However, the company could improve it by implementing additional tests to check the app’s behavior in other locations. At the same time, Apple should more proactively find and remove scam apps from the App Store.
In 2017, Uber was accused of working on a “geofence” for Apple’s headquarters in Cupertino. When the app was run inside this geofence, it automatically disabled codes used to fingerprint and track the user across the web. Even so, it seems that Apple hasn’t done much to prevent other situations like this.
In 2021, documents revealed that the App Store Review team has more than 500 human experts to review more than 100,000 apps every week. Even so, the vast majority of apps go through automated review processes to check if they violate the App Store guidelines before undergoing the manual review process.
Following the publication of our articles, an Apple spokesperson told 9to5Mac that the apps have been removed from the App Store, but no details have been provided about the company’s measures to prevent other apps like this from getting approved.
FTC: We use income earning auto affiliate links. More.

 5 months ago
37
5 months ago
37








 English (US) ·
English (US) ·